None of the existing eCommerce platforms are 100% secure. Each can be breached in multiple ways: via remote access, SQL injection, misconfiguration, etc. Most all eCommerce stores are attractive targets for hackers. Customers might suffer massive loss and identity theft while merchants might encounter damaged brand reputation, loss of merchandise, lawsuit threats, etc.
Despite being an innovative and technically advanced eCommerce solution, Magento is not an exception to security breaches.
Recently, a considerable number of Magento 2.x sites were exposed to hackers.
Magento 2 Vulnerability Issue
A group of hackers from March to May attacked various Magento 2.x sites. The code name of the security flaw is “PRODSECBUG-2198” and is related to its content management system.
The vulnerability was detected as an SQL injection flaw in the Magento CMS, which could be exploited by remote attackers.
SQL Injection Flaw:
“Remote attackers send specially crafted HTTP GET requests to the vulnerable script and execute arbitrary SQL commands in the application’s database. If the SQL commands are executed successfully, it may lead to exploitation of sensitive data as attackers could read, modify, add or delete arbitrary data in the database”.
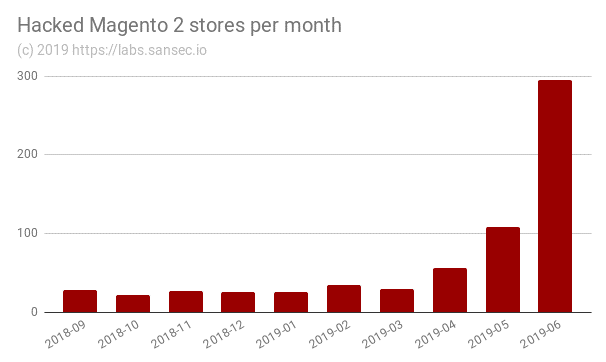
Image Source: https://sansec.io/research/magento-2-hacks
Magento 2 Admin Hack:
As researched by Sansec Threat Research Team, the attackers started focusing on mass-retrieving passwords and usernames of customers from Magento stores. Further, they began implementing skimmers on their assets. So even if merchants/stores have already applied Magento 2’s security patch, attackers could reach their name from the list.
After a few days of the attack, hackers owned one or more admin passwords. So, stage two of the attack was planned to find the actual Magento dashboard login. As Magento uses a random URL for its backend panel, another flaw was exposed wherein the hidden URL could be exposed to anyone.
With the access of admin passwords and the hidden dashboard of Magento, the attackers logged in and added a snippet of malicious JS to design/includes a section of the store. This code behaved like a Magecart attack while it intercepts credit cards and PII from customers as they type them in the text box.
To outline the security issues, Magento 2.4 release brought more than 30 security enhancements. So, it is recommended to update your Magento store to the latest version as early as possible.
Consequences of Magento 2 Vulnerabilities on E-Commerce Stores
- Customers’ complaints regarding stolen credit card information.
- Merchants detect multiple admins having access to the Magento dashboard.
- E-commerce sites are accessed from multiple and unknown IPs.
- The Magento store has been manipulated.
- While scanning the website, merchants found saved credit cards of different customers.
- FTP logs received a successful connection from unknown devices.
- Malicious code is injected into the files redirecting the admin to a phishing page.
- Search engines blacklist many Magento stores.
- Merchants using third-party hosting encountered account suspension.
How can we help you resolve the Magento 2 Vulnerability Issues?
We help you secure the hosting environment, apply security patches, and delete all the unnecessary software on the server. We set the access limitation for the Magento Admin; limit required outgoing connections, all while ensuring that files’ permissions are correct.
Here’s the list of solutions we implement to save your commerce store from getting hacked.
- Follow safe protocol
- Check for signs of attack / Scan Your Store for Malware
- Improve safety by implementing the latest Magento 2 security patches
- Implement secure backup practices
- Make sure all payment processors are PCI Compliant
- Add two-factor authentication to create another layer of security for your users
- Switch to a custom admin URL
- Shield your Magento website from malicious bots
- Shield the store from cross-site scripting attacks
- Prevent MySQL-injections
- Keep your Magento store up to date.
We suggest using a password as safest as you can and change it periodically.
Having hands-on experience in dealing with Magento 2 best security practices, our certified developers will help you maintain your e-commerce site’s longevity. Connect with our team of experts to discuss your website security concerns and their solutions.









